IPsec VPN
We now have a new IPsec VPN app for your HDA.
This VPN stack has many advantages, although it still requires two ports to be forwarded from your router to your HDA. These are
500 UDP and 4500 UDP
UDP, not TCP.
Below is how to set up clients for various client operating systems.
Contents
iOS Setup
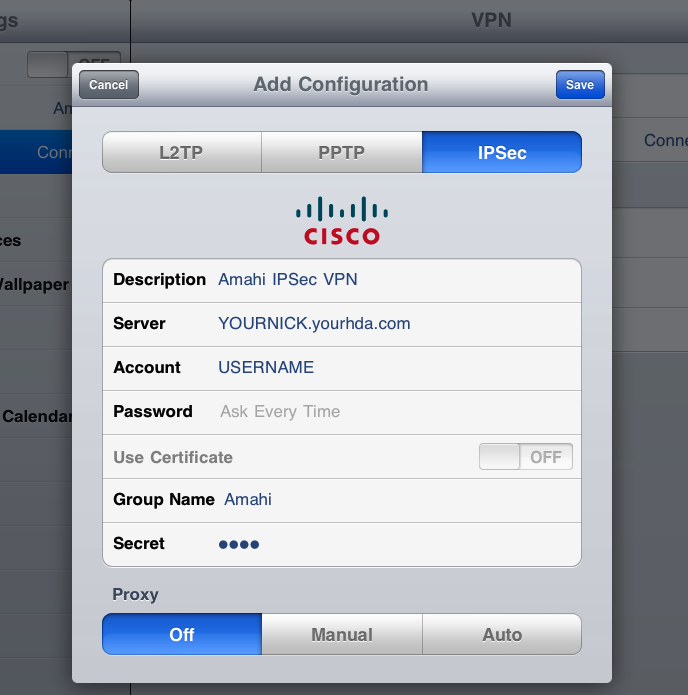
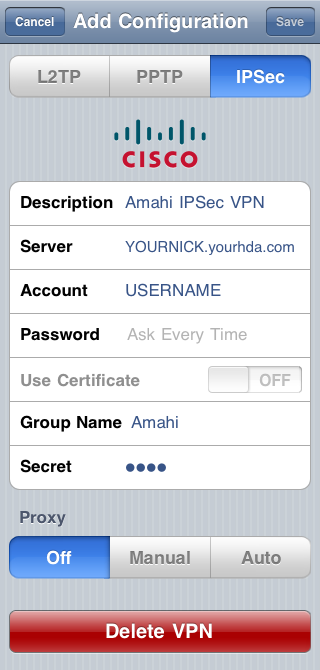
Go to Settings > Network > VPN > IPSec, enter the settings below and click on Save.
- Description: Amahi IPSec VPN
- Server: YOURNICK.yourhda.com (put your Amahi dyndns address, nickname and host)
- Account: USERNAME
- Password: leave it as "Ask Every Time" or put one if you feel it's safe to leave it there
- Use Certificate: leave it as OFF
- Group Name: Amahi (with a capital A)
- Secret: this is the 4-character you got the when you installed the IPSec VPN app in your HDA
- Proxy: leave it as off
Below you can see how the setup area looks in a few Apple iOS devices.
iPad
It should look something like this on the iPad 2, iOS 4.x
iPhone 3, iPod Touch
It should look something like this on the iPhone 3, iOS 4.x
Max OS X Setup
Similar to iOS.
- Open System Preferences > Network
- Click on the + sign to create a new service
- For Interface select VPN. For VPN type select Cisco IPSec'. Give the service a name, like Amahi Home and click on Create
- Once added, select it. In the Server Address put YOURNICK.yourhda.com (replace YOURNICK with your nickname).
- In Account Name, put your username. Leave password empty unless you trust this computer.
- Click on Authentication Settings
- In Shared Secret, put the Group Setting from your internal IPSec VPN. In Group Name, enter Amahi. Click OK
- You can now click on Connect to connect!
- You can also click on "Show VPN status in menu bar" for quick access to the VPN connection
- Click on Apply to save these settings
Advanced Topics
Note: this section requires editing files with root privileges and restarting the racoon daemon.
The pre-shared key is stored in the file /etc/racoon/psk.txt. If you want to customise it for any reason, simply edit the file with your favourite text editor and restart racoon. You will need to manually update all of your clients. Note that the web page at http://ipsec-vpn will not be updated.
Routing all network traffic via the VPN
By default, the VPN will only route traffic destined for your home network via the VPN. General web traffic etc, will *not* be encrypted. To change this behaviour so that all network traffic from your client is routed via your VPN, edit /etc/racoon/racoon.conf and remove the lines beginning "split_network" and "split_dns". The restart racoon.