Difference between revisions of "Key-Based SSH Logins"
| (27 intermediate revisions by 4 users not shown) | |||
| Line 1: | Line 1: | ||
| − | + | This page shows how to create a key based SSH login to your server using the Windows PuTTY client, Mac OS X Terminal.app or Linux. | |
| + | This will allow you to safely login using SSH onto your HDA without having to provide a password every time. | ||
| + | =Windows - PuTTY= | ||
| − | == | + | ==Install Putty and PuttyGen== |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
Download the following files from the [http://www.chiark.greenend.org.uk/%7Esgtatham/putty/download.html PuTTY download] page and save them on your Windows system, e.g. on the desktop: | Download the following files from the [http://www.chiark.greenend.org.uk/%7Esgtatham/putty/download.html PuTTY download] page and save them on your Windows system, e.g. on the desktop: | ||
| Line 18: | Line 14: | ||
Both files are self contained executables. That is: they do not install anything but run from where they are saved. | Both files are self contained executables. That is: they do not install anything but run from where they are saved. | ||
| − | + | ==Create a profile for use with your Amahi HDA== | |
| − | |||
In PuTTY, you can create profiles for connections to your various SSH servers, so you don't have to type in the settings again when you want to connect to a certain server again. | In PuTTY, you can create profiles for connections to your various SSH servers, so you don't have to type in the settings again when you want to connect to a certain server again. | ||
| Line 26: | Line 21: | ||
[[Image:Red-S01.png]] | [[Image:Red-S01.png]] | ||
| − | Now select '''Connection >> Data'' in the | + | Now select '''Connection >> Data'' in the Category box and in the Auto-login box enter the username you wish to login to your HDA with. In this example 'sue'. |
[[Image:Red-S02.png]] | [[Image:Red-S02.png]] | ||
| Line 33: | Line 28: | ||
| − | + | ==Connecting to your HDA using SSH== | |
Now you are on your 'Sessions' screen lets open our session by pressing open. You should see: | Now you are on your 'Sessions' screen lets open our session by pressing open. You should see: | ||
| Line 42: | Line 37: | ||
| − | + | ==Generating a public/private key pair== | |
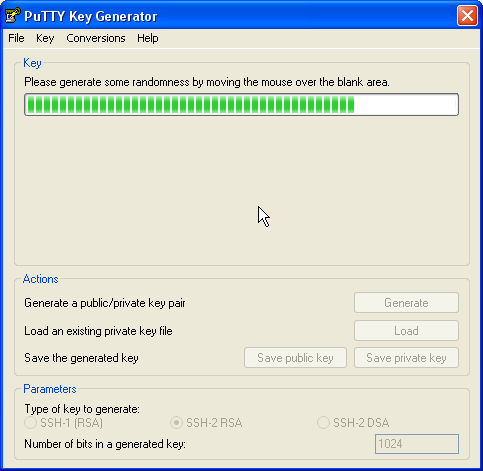
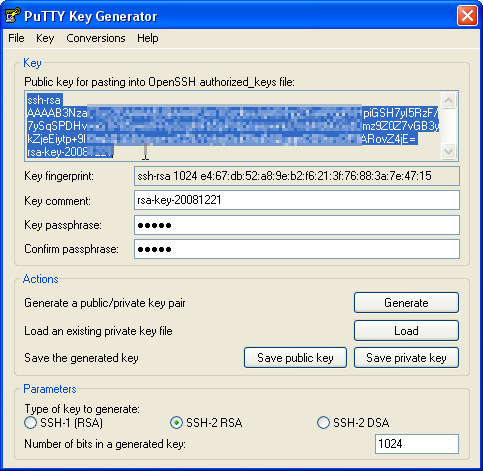
Here we can use PuTTYgen to create a private/public key pair. Start it by double-clicking its executable file. Make sure you select SSH-2 RSA under Type of key to generate and specify 1024 as the Number of bits in a generated key. Then click on Generate: | Here we can use PuTTYgen to create a private/public key pair. Start it by double-clicking its executable file. Make sure you select SSH-2 RSA under Type of key to generate and specify 1024 as the Number of bits in a generated key. Then click on Generate: | ||
| Line 65: | Line 60: | ||
| − | + | ==Save the public key on our Amahi server== | |
Now we must transfer the public key to our Amahi HDA server. Copy the key from the PuttyGEN window: | Now we must transfer the public key to our Amahi HDA server. Copy the key from the PuttyGEN window: | ||
| Line 73: | Line 68: | ||
Using ''putty'' logon to our Amahi HDA using the profile you created earlier. | Using ''putty'' logon to our Amahi HDA using the profile you created earlier. | ||
| + | === Option 1 (Amahi 7 or greater '''ONLY''') === | ||
| + | We can add the key file to the HDA using the HDA dashboard. | ||
| + | |||
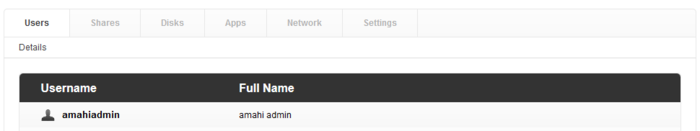
| + | Navigate to the '''Users''' tab | ||
| + | [[File:User-SS0.png|700px]] | ||
| + | |||
| + | Select your user and you should see ''Authentication''. | ||
| + | [[File:User-SS1.png|700px]] | ||
| + | |||
| + | Click the key and paste your key information. Choose ''Update Key'' when finished. | ||
| + | [[File:User-SS2.png|700px]] | ||
| + | |||
| + | Proceed to [[Key-Based_SSH_Logins#Configure_PuTTY_to_use_the_private_key|Configure PuTTY to use the private key]] | ||
| + | |||
| + | === Option 2 (All Amahi versions) === | ||
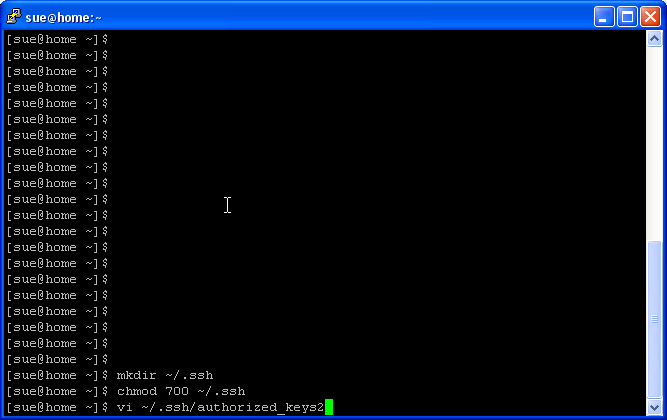
We must now create a directory and file in which to store our public key | We must now create a directory and file in which to store our public key | ||
| Line 89: | Line 99: | ||
<div style="border: 1px solid #A3B1BF; padding: .5em 1em; color: #000; background-color: #E6F2FF; margin: 3px 3px 1em 3px;">chmod 600 ~/.ssh/authorized_keys2</div> | <div style="border: 1px solid #A3B1BF; padding: .5em 1em; color: #000; background-color: #E6F2FF; margin: 3px 3px 1em 3px;">chmod 600 ~/.ssh/authorized_keys2</div> | ||
| − | + | ==Configure PuTTY to use the private key== | |
| − | |||
Close down your shell to your HDA and restart ''putty'' and load your ''192.168.1.67'' profile | Close down your shell to your HDA and restart ''putty'' and load your ''192.168.1.67'' profile | ||
| Line 96: | Line 105: | ||
[[Image:Red-S01.png]] | [[Image:Red-S01.png]] | ||
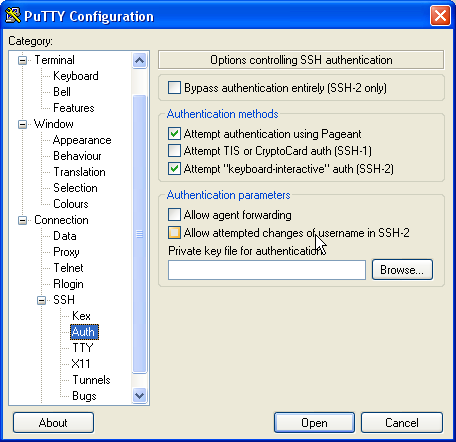
| − | Go to ''''' | + | Go to '''''SSH >> Auth''''' and click on '''''Browse''''' |
[[Image:Red-S10.png]] | [[Image:Red-S10.png]] | ||
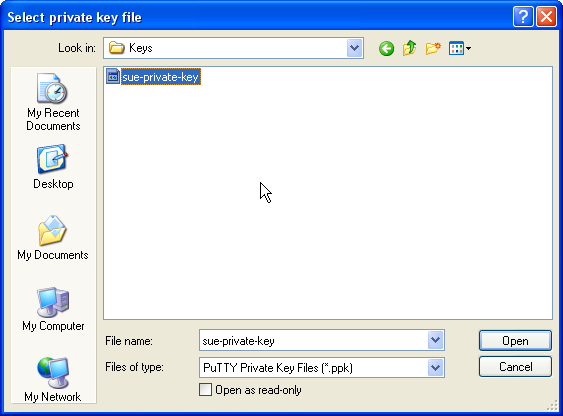
| − | + | Browse to the folder where you saved your keys and select the private key. The one with the '''''ppk''''' suffix. | |
[[Image:Red-S11.png]] | [[Image:Red-S11.png]] | ||
| Line 111: | Line 120: | ||
| − | + | ==Our key-based logon== | |
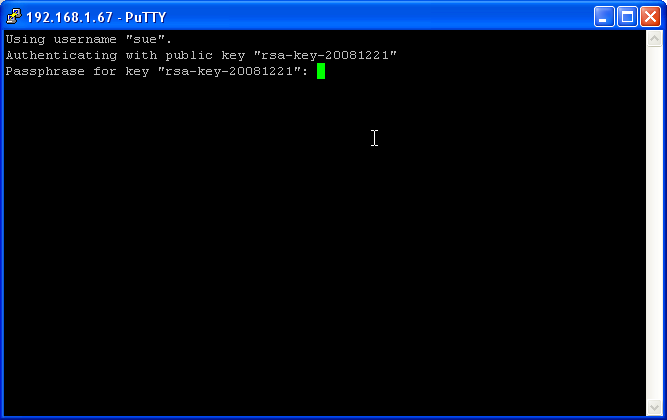
| − | Now on our | + | Now on our PuTTY sessions screen load your '''192.168.1.67''' profile and press ''Open''. You should get: |
[[Image:Red-S12.png]] | [[Image:Red-S12.png]] | ||
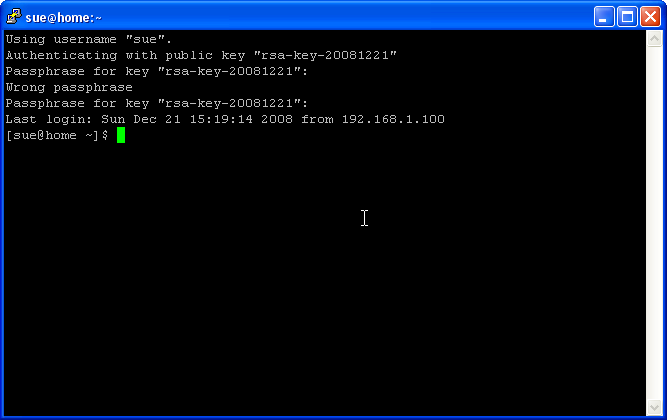
| − | Enter | + | Enter your passphrase that you created when generating your keys. |
[[Image:Red-S12a.png]] | [[Image:Red-S12a.png]] | ||
| + | =Mac OS X - Terminal.app= | ||
| − | + | ==Open Terminal.app== | |
| + | You can find Terminal.app in your Applications > Utilities folder. | ||
| + | |||
| + | ==Generating a public/private key pair== | ||
| + | To generate a new SSH key in a client computer used to login to Amahi, do this: | ||
| + | <div style="border: 1px solid #A3B1BF; padding: .5em 1em; color: #000; background-color: #E6F2FF; margin: 3px 3px 1em 3px;"> | ||
| + | ssh-keygen -t rsa -C "your-email@yourdomain.com" | ||
| + | </div> | ||
| + | |||
| + | It should say something like this (on Mac OS X). Press enter to choose the default: | ||
| + | <div style="border: 1px solid #A3B1BF; padding: .5em 1em; color: #000; background-color: #E6F2FF; margin: 3px 3px 1em 3px;"> | ||
| + | Generating public/private rsa key pair. | ||
| + | Enter file in which to save the key (/Users/YOURUSERNAME/.ssh/id_rsa): | ||
| + | </div> | ||
| + | |||
| + | Enter a passphrase. It's not secure to leave it empty. To avoid having to enter the passphrase every time you can use the [https://en.wikipedia.org/wiki/Apple_Keychain Mac OS Keychain] in Mac OS or an ssh-agent on Linux: | ||
| + | <div style="border: 1px solid #A3B1BF; padding: .5em 1em; color: #000; background-color: #E6F2FF; margin: 3px 3px 1em 3px;"> | ||
| + | Enter passphrase (empty for no passphrase): | ||
| + | </div> | ||
| + | |||
| + | Then enter it again | ||
| + | <div style="border: 1px solid #A3B1BF; padding: .5em 1em; color: #000; background-color: #E6F2FF; margin: 3px 3px 1em 3px;"> | ||
| + | Enter same passphrase again: | ||
| + | </div> | ||
| + | |||
| + | This will give you something like this: | ||
| + | <div style="border: 1px solid #A3B1BF; padding: .5em 1em; color: #000; background-color: #E6F2FF; margin: 3px 3px 1em 3px;"> | ||
| + | Your identification has been saved in /Users/YOURUSERNAME/.ssh/id_rsa. | ||
| + | Your public key has been saved in /Users/YOURUSERNAME/.ssh/id_rsa.pub. | ||
| + | The key fingerprint is: | ||
| + | f1:2b:ae:c0:64:0c:57:6a:46:da:6a:ec:db:8c:a2:06 your-email@yourdomain.com | ||
| + | </div> | ||
| + | |||
| + | and it may also show a randomart image (not used very often yet). | ||
| + | |||
| + | ==Save the public key on our Amahi server== | ||
| + | |||
| + | Now we must transfer the public key to our Amahi HDA server. | ||
| + | |||
| + | Execute the following command, in Terminal.app: | ||
| + | |||
| + | <div style="border: 1px solid #A3B1BF; padding: .5em 1em; color: #000; background-color: #E6F2FF; margin: 3px 3px 1em 3px;"> | ||
| + | scp ~/.ssh/id_rsa.pub your_username@hda:.</div> | ||
| + | |||
| + | Replace ''your_username'' with the username you created on Fedora.<br/> | ||
| + | If your HDA is not yet setup, you might have to replace ''hda'' by your HDA' IP address too.<br/> | ||
| + | When prompted, enter the associated password. | ||
| + | |||
| + | Then, we must copy that public key into the ''authorized_keys'' file. | ||
| + | |||
| + | <div style="border: 1px solid #A3B1BF; padding: .5em 1em; color: #000; background-color: #E6F2FF; margin: 3px 3px 1em 3px;">ssh your_username@hda<br /> | ||
| + | mkdir ~/.ssh<br /> | ||
| + | chmod 700 ~/.ssh<br /> | ||
| + | mv id_rsa.pub .ssh/authorized_keys2</div> | ||
| + | |||
| + | Now to make that file accessible by only the user | ||
| + | |||
| + | <div style="border: 1px solid #A3B1BF; padding: .5em 1em; color: #000; background-color: #E6F2FF; margin: 3px 3px 1em 3px;">chmod 600 ~/.ssh/authorized_keys2</div> | ||
| + | |||
| + | =Linux= | ||
| + | |||
| + | Follow the [[#Mac_OS_X_-_Terminal.app|Mac OS X instructions]], but use a standard terminal (Applications > System Tools > Terminal in Fedora). | ||
| + | |||
| + | =Additional Security Settings= | ||
Up to now, you can log in with your private/public key pair and still with username/password logins, so if someone doesn't attach a private key to his PuTTY session, he will be asked for a username and password. So to achieve a better security, we must disable the username/password logins (you should do this only when you know that your key-based logins are working, because if they aren't and you disable username/password logins, then you have a problem...). | Up to now, you can log in with your private/public key pair and still with username/password logins, so if someone doesn't attach a private key to his PuTTY session, he will be asked for a username and password. So to achieve a better security, we must disable the username/password logins (you should do this only when you know that your key-based logins are working, because if they aren't and you disable username/password logins, then you have a problem...). | ||
| Line 132: | Line 205: | ||
<div style="border: 1px solid #A3B1BF; padding: .5em 1em; color: #000; background-color: #E6F2FF; margin: 3px 3px 1em 3px;">su -<br /> | <div style="border: 1px solid #A3B1BF; padding: .5em 1em; color: #000; background-color: #E6F2FF; margin: 3px 3px 1em 3px;">su -<br /> | ||
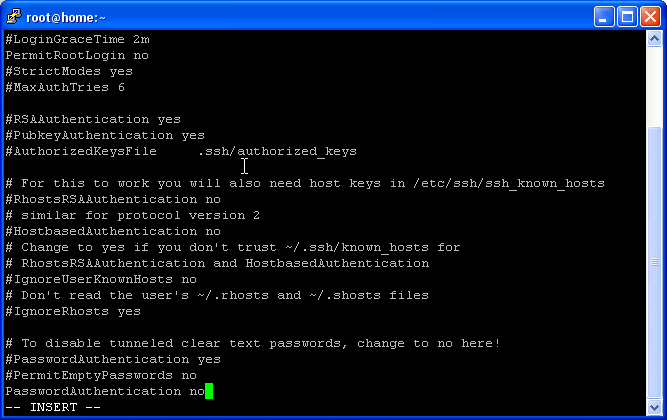
| − | vi /etc/ | + | vi /etc/ssh/sshd_config</div> |
[[Image:Red-S13.png]] | [[Image:Red-S13.png]] | ||
| Line 139: | Line 212: | ||
<div style="border: 1px solid #A3B1BF; padding: .5em 1em; color: #000; background-color: #E6F2FF; margin: 3px 3px 1em 3px;"> | <div style="border: 1px solid #A3B1BF; padding: .5em 1em; color: #000; background-color: #E6F2FF; margin: 3px 3px 1em 3px;"> | ||
service sshd restart</div> | service sshd restart</div> | ||
| + | |||
| + | = Tips = | ||
| + | |||
| + | * Recommend you check out [[Secure_SSH_against_brute_force_attacks|secure SSH against brute force attacked]] guidance to protect your HDA. | ||
| + | |||
| + | * Monitor SSH access to your HDA by following the [[SSH_Email_Alerts|SSH email alerts]] tutorial. | ||
| + | |||
| + | * In Amahi 7, you can add the '''public''' (not the private key) in your Users area of the HDA dashboard. | ||
| + | |||
| + | [[File:SSH_keys.png]] | ||
Latest revision as of 02:41, 25 March 2016
This page shows how to create a key based SSH login to your server using the Windows PuTTY client, Mac OS X Terminal.app or Linux.
This will allow you to safely login using SSH onto your HDA without having to provide a password every time.
Contents
- 1 Windows - PuTTY
- 2 Mac OS X - Terminal.app
- 3 Linux
- 4 Additional Security Settings
- 5 Tips
Windows - PuTTY
Install Putty and PuttyGen
Download the following files from the PuTTY download page and save them on your Windows system, e.g. on the desktop:
http://the.earth.li/~sgtatham/putty/latest/x86/putty.exe
http://the.earth.li/~sgtatham/putty/latest/x86/puttygen.exe
Both files are self contained executables. That is: they do not install anything but run from where they are saved.
Create a profile for use with your Amahi HDA
In PuTTY, you can create profiles for connections to your various SSH servers, so you don't have to type in the settings again when you want to connect to a certain server again.
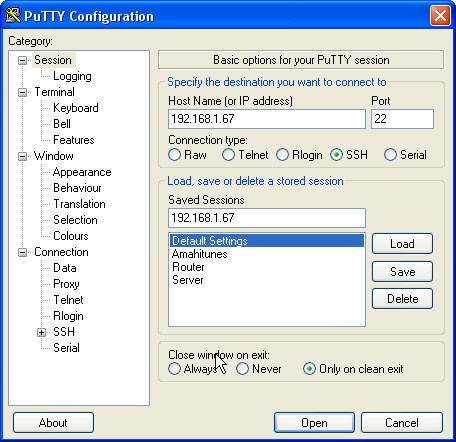
Now we will create a profile for our 192.168.1.67 server. Start PuTTY by double-clicking its executable file. You are now in the category Session (see the tree on the left side of the screenshot). Enter 192.168.1.67 under Host Name (or IP address), enter 22 under Port and select SSH under Protocol.
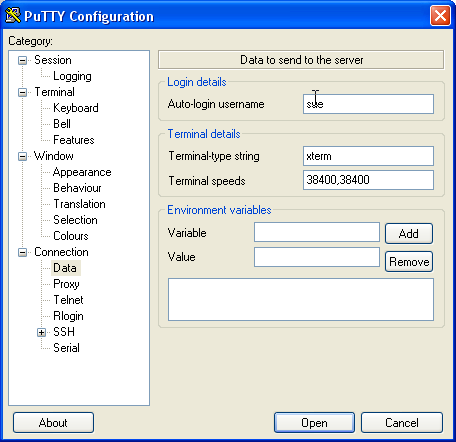
Now select 'Connection >> Data in the Category box and in the Auto-login box enter the username you wish to login to your HDA with. In this example 'sue'.
Once this is done return to your Sessions and give your profile a meaningful name and press save. Anytime in the future you can click on your profile name a Open and your session is opened. You will appreciate this more later.
Connecting to your HDA using SSH
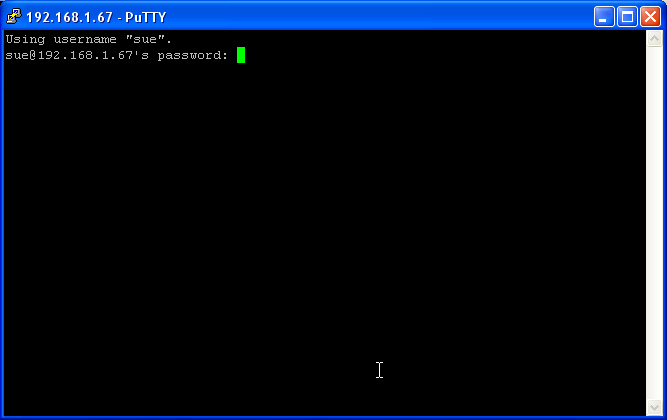
Now you are on your 'Sessions' screen lets open our session by pressing open. You should see:
Type in the users password and you have your ssh xterm ready to go. Now this was the normal way of logging in but being a password system it is open to brute force attacks.
Generating a public/private key pair
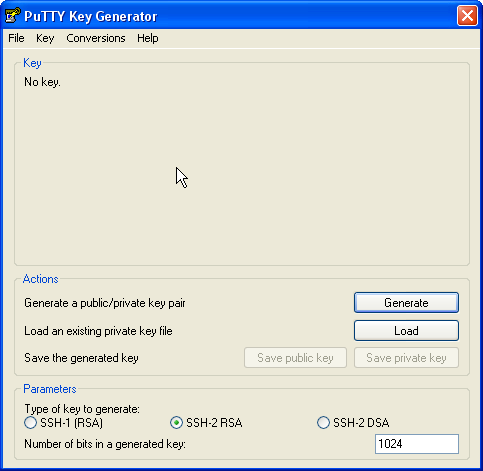
Here we can use PuTTYgen to create a private/public key pair. Start it by double-clicking its executable file. Make sure you select SSH-2 RSA under Type of key to generate and specify 1024 as the Number of bits in a generated key. Then click on Generate:
Move your mouse about randomly to generate the randomness.
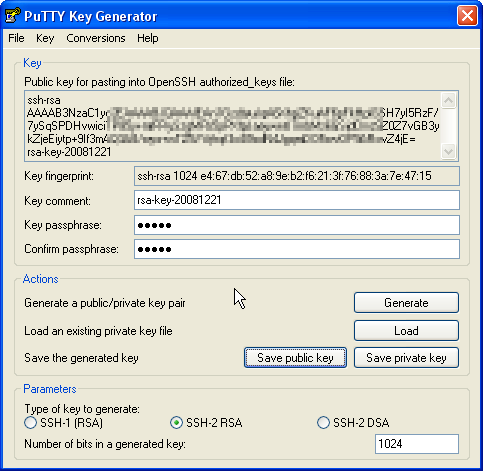
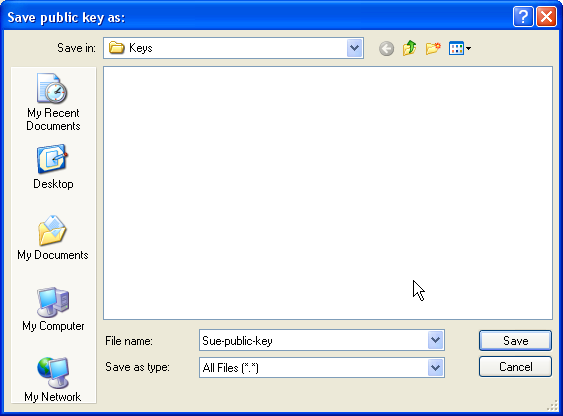
Now a private/public key pair has been generated. Under Key comment, you can enter any comment; normally you use your email address here. Then specify a Key passphrase and repeat it under Confirm passphrase. You'll need that passphrase to log in to SSH with your new key. Then click on Save public key and save it in some safe location on your computer. You are free to choose a filename and extension, but it should be one that lets you remember for which system it is.
Then click on Save public key and save it in some safe location on your computer. You are free to choose a filename and extension, but it should be one that lets you remember for which system it is.
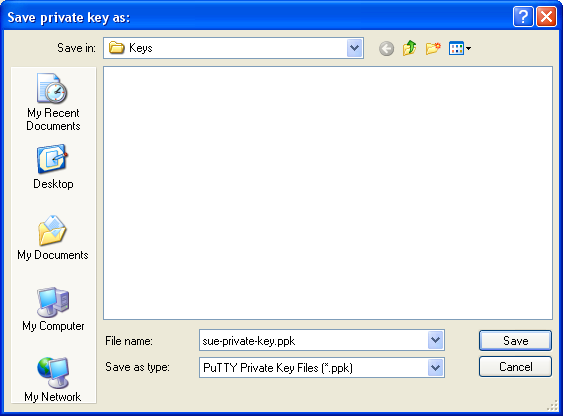
Then click on Save private key. You can save it in the same location as the public key - it should be a location that only you can access and that you don't lose! (If you lose the keys and have disabled username/password logins, then you can't log in anymore!) Again, you're free to choose a filename, but this time the extension must be .ppk:
Save the public key on our Amahi server
Now we must transfer the public key to our Amahi HDA server. Copy the key from the PuttyGEN window:
Using putty logon to our Amahi HDA using the profile you created earlier.
Option 1 (Amahi 7 or greater ONLY)
We can add the key file to the HDA using the HDA dashboard.
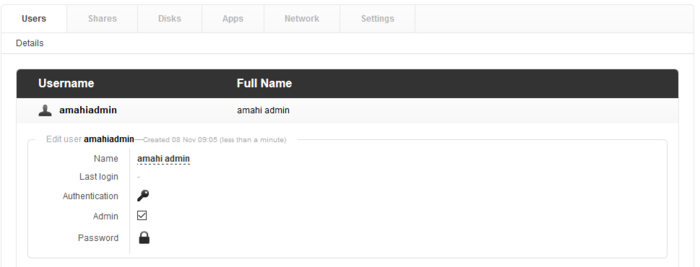
Select your user and you should see Authentication.
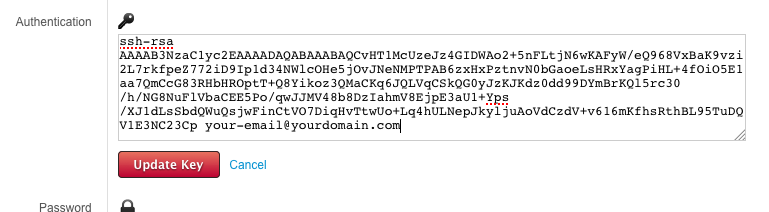
Click the key and paste your key information. Choose Update Key when finished.
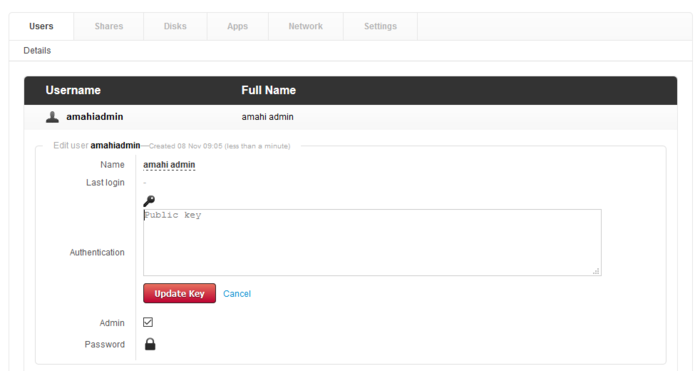
Proceed to Configure PuTTY to use the private key
Option 2 (All Amahi versions)
We must now create a directory and file in which to store our public key
chmod 700 ~/.ssh
And open our file that will store our key
Type I to enter insert mode. Paste your copied key (just a right click of the mouse was enough for me. Then <Escape> :wq to exit edit mode, write the file and quit. This file may already exist if you have used ssh before.
Now to make that file accessible by only the user
Configure PuTTY to use the private key
Close down your shell to your HDA and restart putty and load your 192.168.1.67 profile
Go to SSH >> Auth and click on Browse
Browse to the folder where you saved your keys and select the private key. The one with the ppk suffix.
Go back to your Session tab and click save.
Our private key is now attached to our profile
Our key-based logon
Now on our PuTTY sessions screen load your 192.168.1.67 profile and press Open. You should get:
Enter your passphrase that you created when generating your keys.
Mac OS X - Terminal.app
Open Terminal.app
You can find Terminal.app in your Applications > Utilities folder.
Generating a public/private key pair
To generate a new SSH key in a client computer used to login to Amahi, do this:
ssh-keygen -t rsa -C "your-email@yourdomain.com"
It should say something like this (on Mac OS X). Press enter to choose the default:
Generating public/private rsa key pair. Enter file in which to save the key (/Users/YOURUSERNAME/.ssh/id_rsa):
Enter a passphrase. It's not secure to leave it empty. To avoid having to enter the passphrase every time you can use the Mac OS Keychain in Mac OS or an ssh-agent on Linux:
Enter passphrase (empty for no passphrase):
Then enter it again
Enter same passphrase again:
This will give you something like this:
Your identification has been saved in /Users/YOURUSERNAME/.ssh/id_rsa. Your public key has been saved in /Users/YOURUSERNAME/.ssh/id_rsa.pub. The key fingerprint is: f1:2b:ae:c0:64:0c:57:6a:46:da:6a:ec:db:8c:a2:06 your-email@yourdomain.com
and it may also show a randomart image (not used very often yet).
Save the public key on our Amahi server
Now we must transfer the public key to our Amahi HDA server.
Execute the following command, in Terminal.app:
Replace your_username with the username you created on Fedora.
If your HDA is not yet setup, you might have to replace hda by your HDA' IP address too.
When prompted, enter the associated password.
Then, we must copy that public key into the authorized_keys file.
mkdir ~/.ssh
chmod 700 ~/.ssh
Now to make that file accessible by only the user
Linux
Follow the Mac OS X instructions, but use a standard terminal (Applications > System Tools > Terminal in Fedora).
Additional Security Settings
Up to now, you can log in with your private/public key pair and still with username/password logins, so if someone doesn't attach a private key to his PuTTY session, he will be asked for a username and password. So to achieve a better security, we must disable the username/password logins (you should do this only when you know that your key-based logins are working, because if they aren't and you disable username/password logins, then you have a problem...).
To disable the username/password logins, we must modify the sshd configuration file. On our Fedora based Amahi system, it's /etc/ssh/sshd_config. You should set Protocol to 2 (1 is insecure and should not be used!), PasswordAuthentication to no.
Login as root:
vi /etc/ssh/sshd_config
You will now need to restart you SSH server
Tips
- Recommend you check out secure SSH against brute force attacked guidance to protect your HDA.
- Monitor SSH access to your HDA by following the SSH email alerts tutorial.
- In Amahi 7, you can add the public (not the private key) in your Users area of the HDA dashboard.